Telnet is a very useful application that has existed in the computer world for decades. It can be used to connect to remote servers for various purposes, such as remotely administering a machine via a Telnet server or manually managing the data stream returned from a web server.
Steps
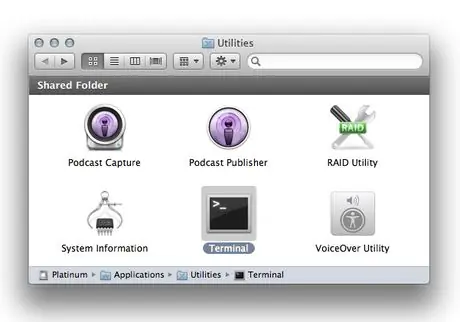
Step 1. Go to the 'Applications' panel, then to the 'Utilities' panel and select the 'Terminal' icon
This application is very similar to the command prompt you find in Windows systems but, since OS X is based on Unix and not MS-Dos, some commands are slightly different
Method 1 of 1: Connect via SSH
Step 1. Use the SSH protocol to create secure connections
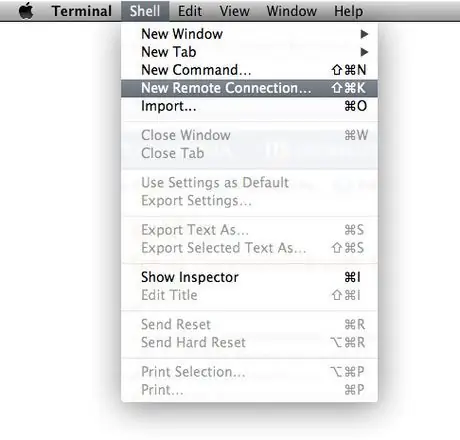
Step 2. From the 'Shell' menu, select the 'New remote connection' item
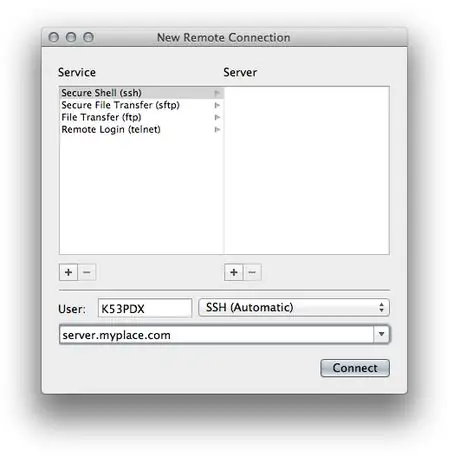
Step 3. Enter the host name or IP address
Enter the address of the server you want to connect to in the field at the bottom of the 'New remote connection' panel.
Note that you will need to have a userID and password in order to access the remote server
Step 4. Click the 'Connect' button
Step 5. You will be prompted for a password
For security reasons, the characters you type will not be shown on the screen.
Step 6. Save the data
Click the '+' button for the 'Server' column.
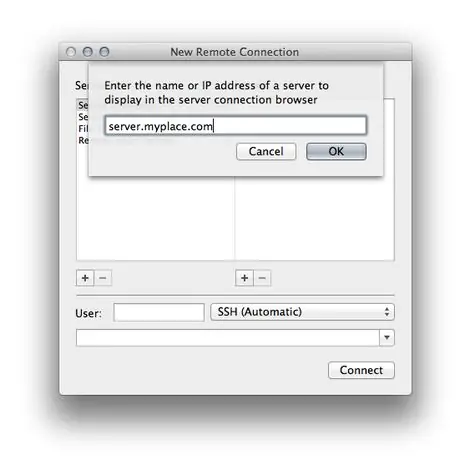
Step 7. When you see the prompt pop up shown in the photo, enter the host name or IP address
Step 8. Click the 'OK' button
Step 9. Enter the userID for the connection in the 'User' field
Click the 'Connect' button and your information will be saved.
Insecure connection
-
Use the 'Command-N' key combination to start a new 'Terminal' session.

Terminal_Window_OSX -
Enter the host name or IP address. Now, next to the blinking cursor, enter the following command: 'telnet server.myplace.net 23' (without quotes).
Note: The port number may vary depending on the service you connect to. Contact the server administrator if the connection fails
Advice
- The port number may not be necessary.
- To terminate the connection use the key sequence CTRL +], type 'quit' and press enter.
Warnings
- Most servers keep track of all Telnet connections and authentication errors, to prevent this tool from being used for non-legal purposes.
- Insecure connections can be intercepted very easily. Use them very carefully.






