Downloading from torrents is one of the simplest ways to get any type of file. Unfortunately, for the underlying structure of torrent data transfers it is also very easy to download viruses or be caught spreading copyrighted material, illegal activity practically all over the world. However, with the right precautions, the risk of your computer getting infected with a virus or someone catching you illegally downloading copyrighted material goes down considerably.
Steps
Part 1 of 2: Avoid Viruses

Step 1. Make sure you have antivirus software installed on your computer
A good antivirus program will help you in thwarting malicious torrents. The Windows operating system integrates "Windows Defender", perfect antivirus software and sufficient to detect and eliminate most viruses. To enable "Windows Defender" protection, go to your computer's "Control Panel" (make sure, however, that you have not installed any other programs of this type). If you prefer, you can install third party antivirus software, such as "BitDefender" or "Kaspersky". Regardless of your choice, only one antivirus software will have to be active on the system for protection to be effective.
Refer to this guide for more information on how to install an antivirus program
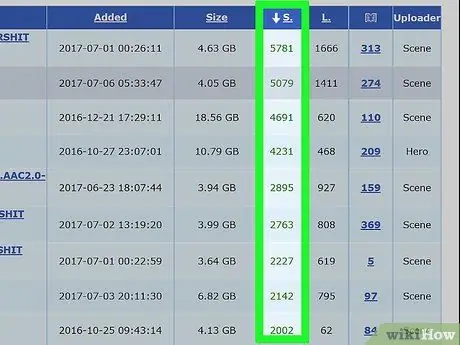
Step 2. Look for torrents that have a large number of seeders
Normally, if a torrent is owned and shared by a large number of users, it means that it is the original file and therefore virus-free. This information is reliable since all other users in possession of the file have already verified that it is the correct one and free from viruses, thus being able to share it without problems. While this is not an absolute guarantee, using this information will help you discard any torrents that seem less reliable. Focusing on files shared by a large number of users results in a higher transfer speed, which is another very interesting advantage.
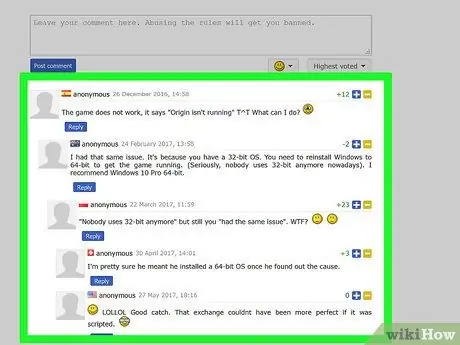
Step 3. Check the comments before proceeding to download
This is also not a foolproof solution, but reading other users' comments regarding the torrent in question can help you determine if it contains a virus or other type of computer security threat. If the number of comments is large, but none refer to viruses or malware, the chances are that it is the correct file. If a large number of comments refer to the presence of a virus, it is most likely a torrent to avoid.
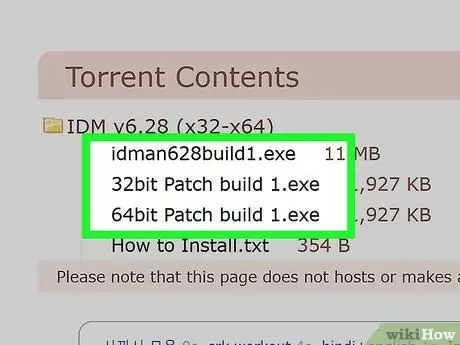
Step 4. Do not download file formats that may contain viruses
Try not to download torrent files related to executable programs. The "EXE" and "BAT" files are the most used formats for the spread of computer viruses. The programs used to violate the anti-piracy protections of video games and other software are the most dangerous to download via torrents.
Step 5. Join a private community of users who share torrents
If you manage to join one of these private groups, the chances of downloading an infected torrent are much lower. All torrents shared within the user community were in fact created and shared by the same members. These torrent files should therefore be much safer and more reliable. Getting into these groups, however, can be very difficult. Normally you need to know a member who can invite you to join; the best way to do this is to be an active member of several online communities and to become friends with someone who already has access to a group like the one you are interested in.
Part 2 of 2: Avoid Being Detected
Step 1. Understand how torrents work
When you download a torrent file, your IP address is made public to all users who share the file in question. This mechanism is essential for the torrent client you are using to connect to that of other users. However, this exposes you to the risk of being identified by the institutions that control the traffic generated by torrents. These regulators include your internet connection provider (ISP) and government copyright agencies. To reduce the risk of being detected by these regulators or of your ISP reducing the bandwidth of your connection, there are several precautions you can take.
Step 2. Install "PeerBlock"
It is a program that blocks IP addresses known to be tied to these control bodies. "PeerBlock" prevents the computer from being able to connect to these addresses; essentially, it prevents the computers of these entities from controlling your torrent-related data traffic. Note that this is not a solution that guarantees you will not be detected. Furthermore, your ISP will always be able to provide information about your internet traffic to the relevant institutions, should they request it. However, it is a simple and quick solution to implement, which greatly minimizes the risk of running into legal problems.
You can download "PeerBlock" for free from the following URL peerblock.com. To install and start "PeerBlock", follow the instructions that will appear on the screen once the installation program is started. "PeerBlock" runs in the background preventing your computer from connecting to certain IP addresses. To get basic protection from the program, choose to use the "P2P" list provided by "Bluetack" during the initial setup process
Step 3. Consider using a VPN service
To completely hide your internet traffic from prying eyes you will need to use a VPN ("Virtual Private Network") service. Normally this type of service is provided via a paid subscription, but as a result your internet traffic will be completely invisible to anyone. Even your ISP will no longer be able to monitor your data traffic, and consequently will not be able to take any type of action against you. The regulators will no longer be able to discover your public IP address and therefore will not be able to monitor your activities or take legal action against you.
There are downsides to using a VPN service. The first obviously is that it is not free, so the relationship between price and acquired benefits must be carefully evaluated. The speed of the internet connection decreases, as the traffic must first be directed to the VPN server which will then route it to the computer. In the event that (most likely) you need to connect to VPN servers physically located in another country, the speed of the internet connection could decrease significantly. Finally, some VPN services may keep track of your activities if regulatory institutions require it for legal purposes. However, there are VPN services that do not track their customers' traffic
Step 4. Choose a VPN service that suits your needs and create an account
Availability is very wide and each service has its own offers, prices and privacy management policies. Make sure you carefully read all the terms in the VPN service agreement you are interested in. You should choose a VPN service that keeps detailed activity logs. Also, remember that not all VPN services allow you to download torrent files. Below is a small list of the most used VPN services, but remember that with a quick Google search you will be able to spot many of them. Do not use free VPN and Proxy services, as they can be unsafe and unreliable. Many VPN services operate from countries whose data retention laws are very lax.
- PrivateInternetAccess.
- TorGuard.
- IPVanish.
- IVPN.
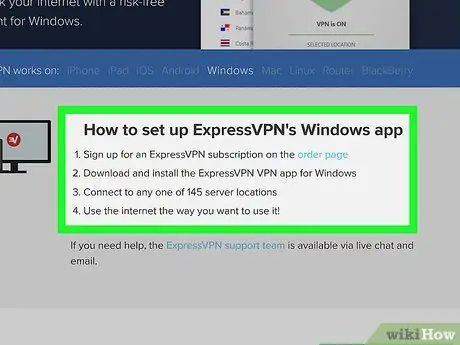
Step 5. Find the information you need to establish the VPN connection
During the registration process for the service, you will be provided with the information necessary to connect to the VPN network of the chosen provider. This data includes the address of the VPN server to connect to and of course the username and password to use. To get this information, you may need to log in directly to the website of the VPN service.
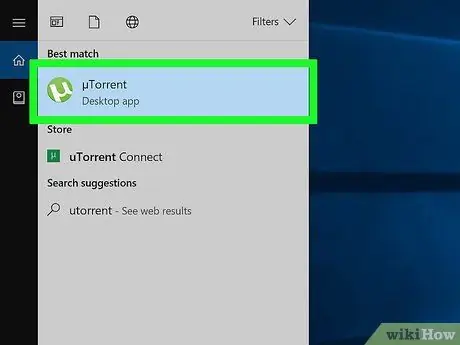
Step 6. Start your torrent client
After you have successfully signed up for your chosen VPN service, you will need to configure the torrent client to take advantage of the VPN connection.
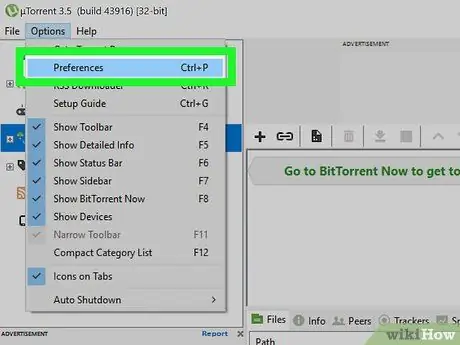
Step 7. Access the program's "Options" or "Preferences" page
Normally this item is placed in the "Tools" menu or in the "Options" menu available at the top of the client window.
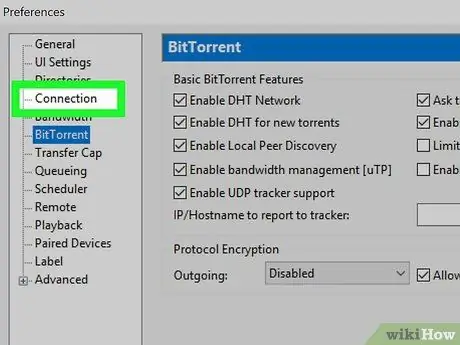
Step 8. Go to the "Connection" tab
This screen allows you to change the settings relating to the connection, including configuring the use of a VPN.
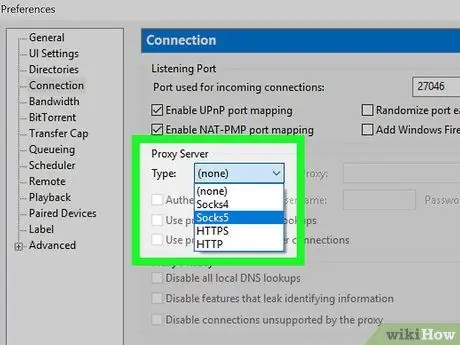
Step 9. Choose the connection protocol used by your VPN service
To do this, access the "Type" menu located in the "Server Proxy" section. Most VPN services use the "SOCKS5" protocol. If in doubt, check the connection information that was provided to you by the service provider.
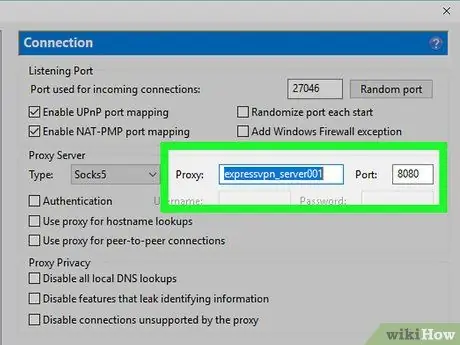
Step 10. Enter the address and port of the VPN server you need to connect to
You can find this information directly on the VPN provider's website after logging in with your account. Many VPN providers offer the ability to connect to different servers in order to offer you a fast connection speed.
Make sure the "Use proxy for peer connections" checkbox is checked
Step 11. Start downloading your torrent files
Once you've finished setting up your connection to the VPN service, you'll be ready to start downloading your favorite content anonymously. However, it should be noted that there is no VPN service that can guarantee 100% anonymity, but using this tool the risk that someone can monitor your activities is very low.






