The best way to make sure your database is safe from hackers is to think exactly like one of them. If you were a hacker what kind of information could catch your attention? How could you try to get hold of it? There are many types of databases in the world and many different ways to hack them, but most hackers prefer to try to discover the admin password or perform an exploit (this is a script or program that exploits a specific database vulnerability to access the stored data). If you know how to use SQL code and have the basic knowledge of the structure and operation of a database, you have everything you need to try to hack one.
Steps
Method 1 of 3: Use SQL Injection
Step 1. Find out if the database is vulnerable to this type of attack
In order to use this method, you must be able to manage without problems the commands, structure and functioning of a database. Start your internet browser and use it to access the database login web interface, then type the '(single quote) character into the username field. Finally, hit the "Login" button. If an error message similar to the following "SQL Exception: quoted string not properly terminated" or "invalid character" appears, it means that the database is vulnerable to an "SQL injection" attack.
Step 2. Find the number of columns in the table
Return to the login page of the database (or to any page of the site whose URL ends with the strings "id =" or "catid ="), then click inside the browser address bar. Place the text cursor at the end of the URL, press the spacebar and type the code
order by 1
then press the Enter key. At this point, replace the number 1 with the number 2 and press Enter again. Keep incrementing that number by one until you get an error message. The number before the one that generated the error message represents the number of columns in the table that contains the database login information.
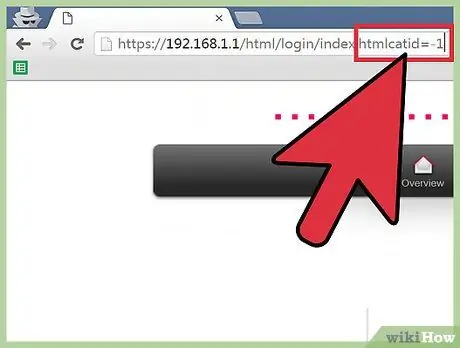
Step 3. Find out which columns accept SQL queries
Place the text cursor at the end of the URL in the browser address bar, then edit the code
catid = 1
or
id = 1
in
catid = -1
or
id = -1
. Press the spacebar and type the code
union select 1, 2, 3, 4, 5, 6
(if the table below is characterized by 6 columns). In this case, you must enter the sequence of numbers corresponding to the columns identified in the previous step and each value must be separated by a comma. Finally, hit the Enter key. You should see as output the numbers corresponding to the columns that accept an SQL query.
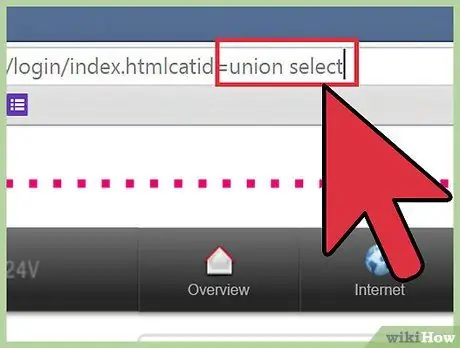
Step 4. Insert the SQL code inside a column
For example, if you want to know the current user and enter the code inside column number 2, delete all characters after the URL string "id = 1" or "catid = 1", then press the space bar. At this point, type in the code
union select 1, concat (user ()), 3, 4, 5, 6--
. Finally, hit the Enter key. The name of the user currently connected to the database should appear on the screen. At this point, you can use any SQL command to get information from the database; for example, you can request a list of all usernames and their passwords registered in the database to violate their respective accounts.
Method 2 of 3: Breaking a Database Administration Password
Step 1. Try logging into the database as an administrator or root user using the default password
By default, some databases do not have a login password for the administrator user (root or admin), so you may be able to log in simply by leaving the password entry field blank. In other cases, the password of the "root" or "admin" account is still the default one which can be found by performing a simple online search in the database support forum.
Step 2. Try using the most common passwords
If access to the database administrator user account is protected with a password (most likely situation), you can try to hack it using the most popular username and password combinations. Some hackers publish lists of passwords that they have been able to locate while carrying out their activities. Try some combinations of usernames and passwords.
- One of the most reliable websites where this type of information can be found is
- Testing passwords by hand is an enormously time-consuming task, but there's nothing wrong with taking a few tries before enlisting the help of much better tools.
Step 3. Use the automatic password verification tools
There are several tools that can test thousands of combinations of words, letters, numbers and symbols in a short time using the method called "brute force" (from the English "brute force") or "exhaustive search" until the password of the correct access.
-
Programs such as DBPwAudit (for Oracle, MySQL, MS-SQL and DB2 databases) and Access Passview (for Microsoft Access databases) are well known and used tools for checking the passwords of the most popular databases in the world. To find new and modern hacking tools designed specifically for the database you want, you can do a Google search. For example, if you need to hack an Oracle database, search online using the following string:
password auditing database oracle
or
password audit tool oracle db
- If you have a login to the server hosting the database to be hacked, you can run a special program called a "hash cracker", such as "John the Ripper", to parse and hack the file that contains the database access passwords. The folder in which this file is stored varies depending on the database in use.
- Remember to download data and programs only from reliable and safe websites. Before using any of the tools you found, do an online search to read reviews from all users who have already used them.
Method 3 of 3: Perform an Exploit
Step 1. Identify an exploit suitable for the database
The Sectools.org website has cataloged all database security tools (including exploits) for more than ten years. These tools are reliable and secure, in fact they are used daily by database and IT system administrators around the world to verify the security of their data. Browse the contents of their "Exploitation" database (or locate another similar website that you trust) to locate the tool or document that will allow you to identify security holes in the database you wish to breach.
- Another such website is www.exploit-db.com. Go to the web page and select the "Search" link, then perform a search for the database you wish to hack (for example "oracle"). Enter the Captcha code that appeared in the appropriate text field, then perform the search.
- Be sure to identify all the exploits you want to try to know what to do in case you can spot a potential security breach.
Step 2. Identify a Wi-Fi network to use as a bridge to attack the database under consideration
To do this, it uses the technique called "wardriving". This involves searching for an unsecured wireless network within a specific area by moving by car, bicycle or on foot and using a suitable radio signal scanner (such as NetStumbler or Kismet). Wardriving is technically a legal procedure; what is illegal is the purpose you want to achieve by using the unsecured wireless network identified by this process.
Step 3. Log into the unsecured network to exploit the database you wish to hack
If you know that what you are about to do is prohibited, obviously it is not a good idea to act directly from your local home network. For this reason, it is necessary to identify an unsecured wireless network, through "wardriving", and then execute the selected exploit without fear of being discovered.
Advice
- Always store sensitive data and personal information within an area of the network protected by a firewall.
- Be sure to password protect access to your Wi-Fi network so that "wardrivers" cannot access your home network to perform an exploit.
- Identify and ask other hackers for advice and useful information. Sometimes the best hacking notions and knowledge can be learned outside the internet.
- There are special programs that automatically perform this kind of attacks. SQLMap is the most popular open source program for testing a site for vulnerability to SQL-Injection attack.
Warnings
- Study the legislation of the country where you live and understand what personal repercussions you could suffer from breaching a database or computer system that you do not own.
- Never try to illegally access a system or database by directly using the internet access of your private network.
- Remember that accessing or hacking a database that you are not the rightful owner of is always an illegal action.






